Return of the Data
Course Map
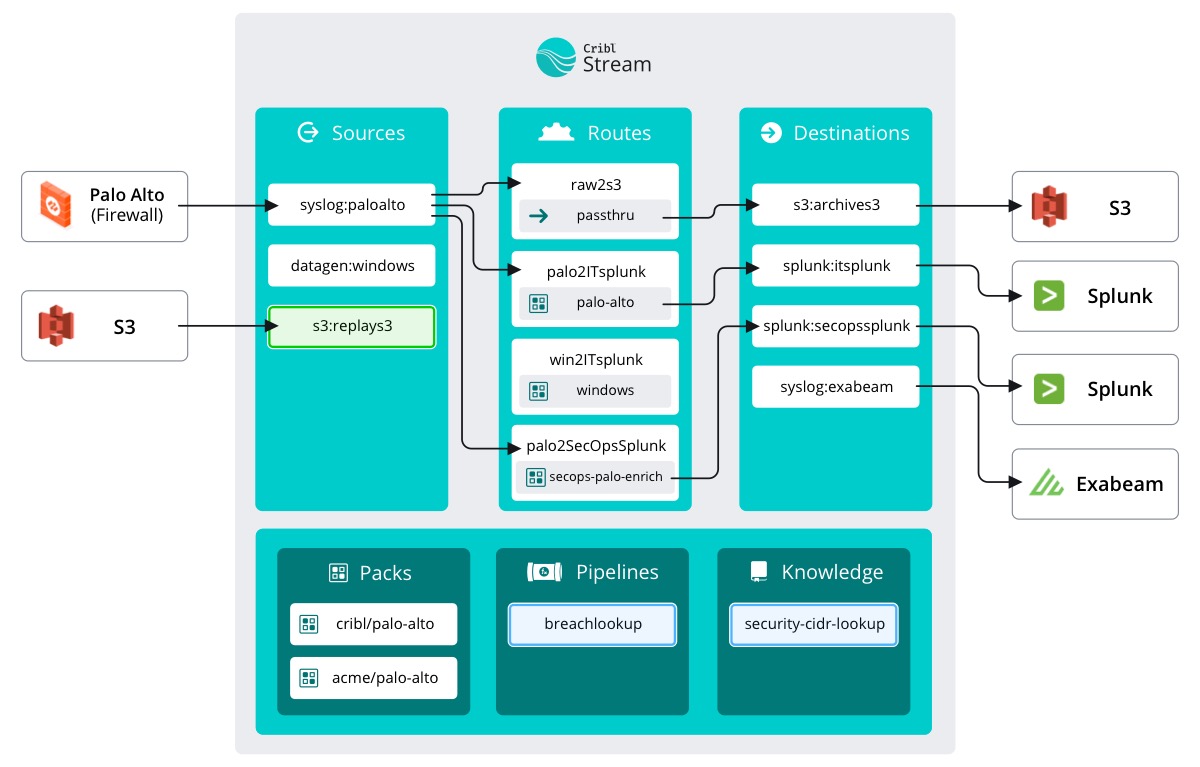
In the Full Fidelity Replay course, we set up the S3 Collector we will be using in this course. Previously, it was used to replay archived data unaltered into a new SIEM. Well, the new SIEM is still in evaluation. Today we are going to use the same Collector to push archived data through our sweet new Pipeline and into the SecOps SIEM.
We don’t need all archived data, though. Ed said they think the breach occurred between May 29 and June 5. Let’s keep that in mind as we configure the S3 Collector.
If you recall from the previous course, we were able to configure the Collector to bypass the Data Routes, saving us some configuration work. We’ll be doing that again here.
important
Configure the s3replay collector
- With
Manageactive in Stream's top nav, select theDatasubmenu and clickSources - Click
S3under Collectors - Click
s3replay - Click
Results Routingon the left side of the window - Make sure
Send to Routesis set toNo - Set the
Pipelineto our newbreachlookup - Change the Destination to
splunk:secopssplunk - Click
Save
All done!
Ed can now search his newly enriched data… as soon as we run the Collector. Let’s go ahead and have the Collector grab the archived data and push it into the SecOps Splunk.
