Function Junction
Course Map
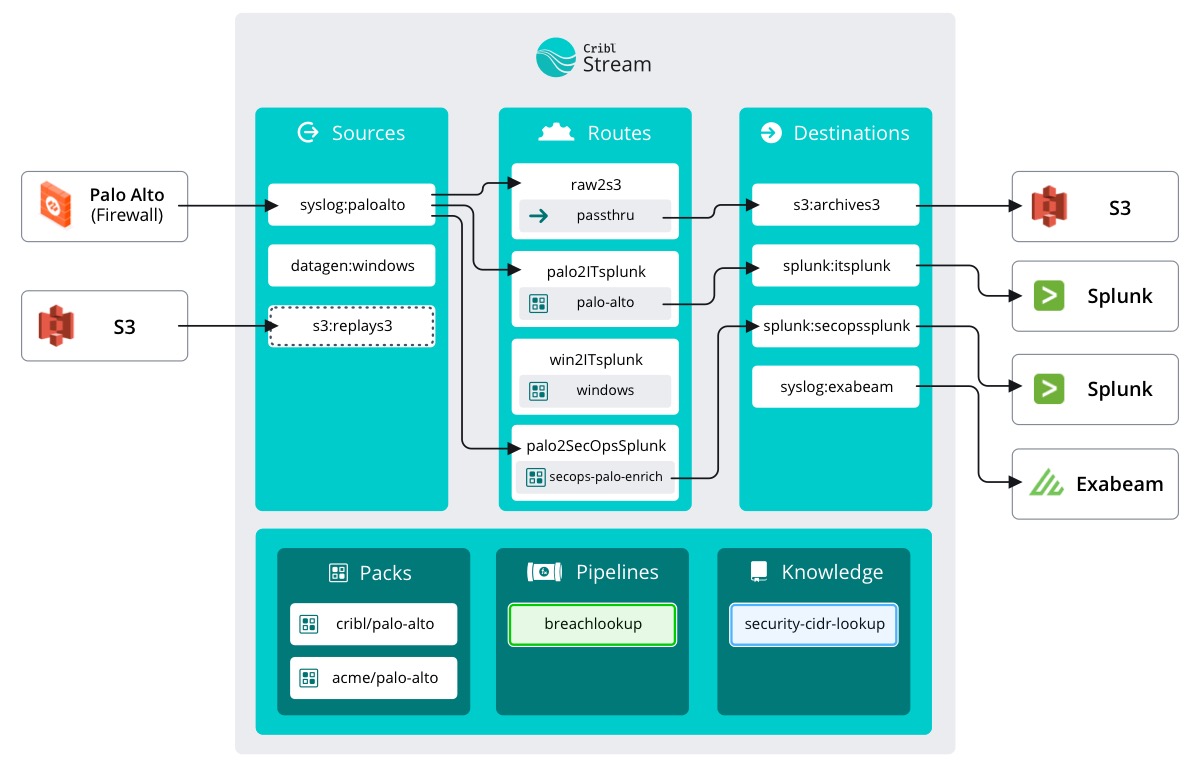
In order to help Ed investigate the breach, we need to create a Pipeline: A series of Functions that transform data.
important
Create a pipeline
- Select the
Processingsubmenu and clickPipelines - Click
+ Pipelinethen clickCreate Pipeline - In the ID field, enter
breachlookup - In the description enter
csv lookup on src and dst ips - Click
Save
Welcome to where the magic (Functions) happens. Some argue that the magic of Stream lies in avoiding vendor lock-in by supporting myriad Sources and Destinations allowing you to connect almost anything to anything. They are also right. But we're here to talk about Functions.
A Function is code that transforms the data inside an event. It can:
- Extract (and label) information from a payload for later use
- Delete erroneous data from an event
- Add important information to an event
- Edit data inside an event to help you better understand it
- Mask sensitive data inside of payloads to ensure no accidental exposure of personal identifiable information (PII) down the line
- Many more!
