Into the Breach
Well, it happened. Acme Corp, the place where we have been working, had a security breach. Not much is known yet, only a breach did happen. Security Operations started investigating it and would like your help. They would like to know how far back this goes. They have also devised a new way of enriching their log data, but can't do it in their SIEM.
note
10:23 [Ed B]: Been looking into the recent breach. I think we narrowed it down to some time between May 29 and June 5.
10:23 [Ed B]: Looks like we need to check the firewall logs again
10:24 [Ed B]: We found something and want to enrich the old data in a new way.
10:24 [Ed B]: We want to label each log src and dst IP based on their CIDR.
10:24 [Ed B]: I have a csv that I’ll send you.
11:00 [Ed B]: Can Stream do that?
Yes. Stream can do that. We’ll have to configure a new Pipeline, but since we sent all raw data to the S3 archive it will be relatively straightforward to replay it through our new Pipeline and into the Splunk Security instance.
Course Map
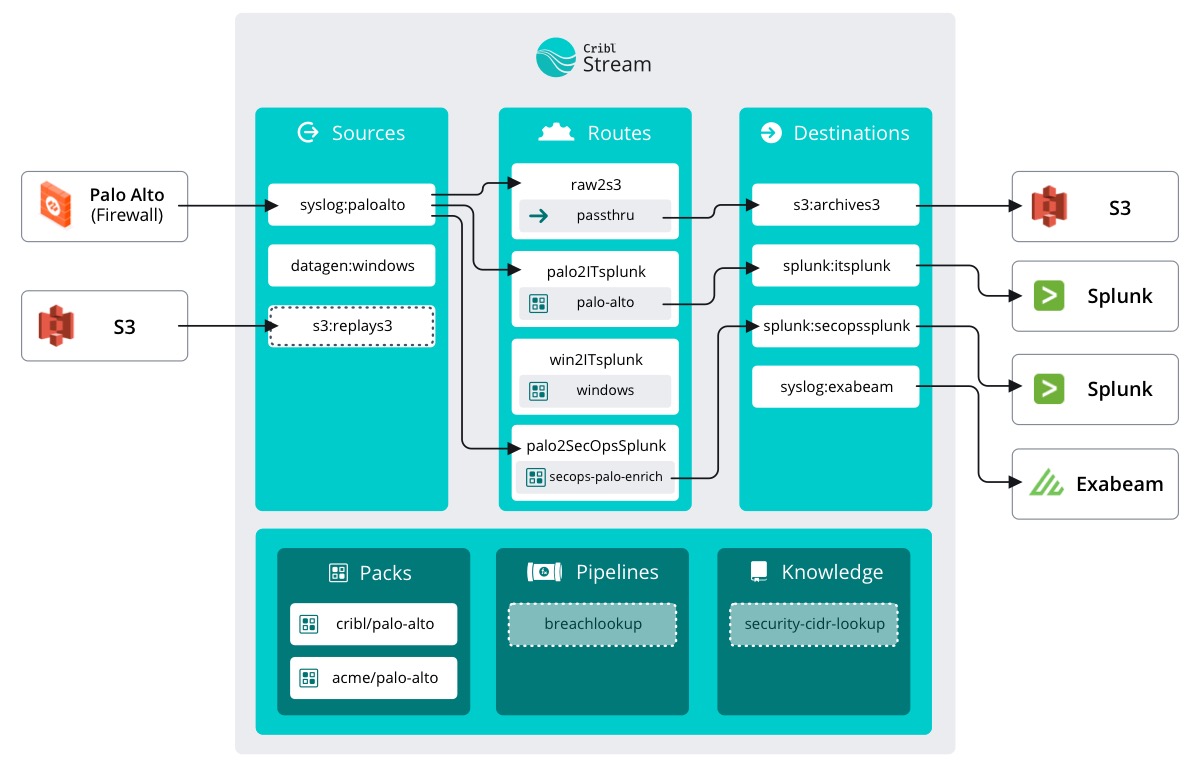
Also, can we just take a moment and appreciate how much our Stream config has grown?
