Course Overview
Cribl, the Data Engine for IT and Security, empowers organizations to transform their data strategy. Customers use Cribl to collect, process, route, and analyze all IT and security data, delivering the flexibility, choice, and control required to adapt to their ever-changing needs. In this tutorial, you will learn how to use Cribl Stream Functions to parse Windows XML events in the stream, and to reduce their volume by 34–70% – dramatically reducing your downstream infrastructure requirements.
This course assumes that you've already gone through the Cribl Stream Overview course. This sandbox has a Cribl Stream instance (which you see at the right) that's already set up with Windows_XML_Events data coming in via a data generator (datagen), and flowing out to a Filesystem Destination (/tmp). There's an empty Pipeline, named XML, which is where we'll be focusing.

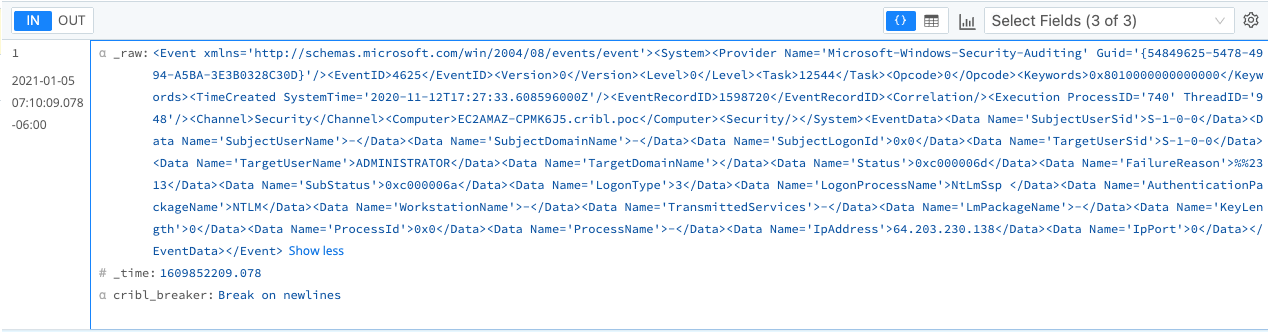
When working with XML, an anonymous Reddit user's quote sums up the challenge: "Some languages can be read by humans, but not by machines, while others can be read by machines but not by humans. XML solves this problem by being readable to neither." Clicking on the Windows XML image below only reinforces this quote:
- Run the following command in the bottom terminal to the right to see the latest events written to the Filesystem Destination.
- If you don't see a terminal window, select the bottom icon that looks like this:
The Command
cat $(ls -t /tmp/XmlWinEventLog:Security/LS-* | head -n 1)
The format of these events is not pretty – each event contains a _raw field with an embedded JSON list of Windows XML Security data. We're going to use Cribl Stream's powerful functions to help you take back control and turn these ugly events into a thing of beauty.
After completing this course, you'll have a better understanding of various Stream built-in functions, including Comment, Eval, Flatten, Rename and Serialize. Best of all, you'll learn how to use Stream's XML parsing function to reduce Windows XML events.
Let's get started!