Snap Pack to Reality
Course Map
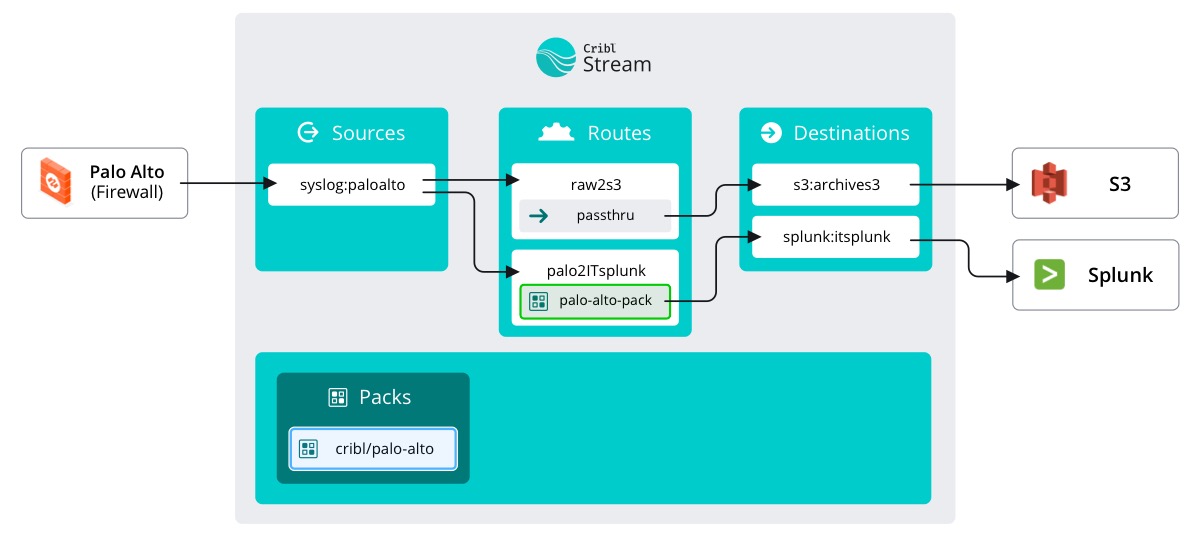
To start, let’s see what IT did to get the Palo Alto traffic into their Splunk instance.
important
Look at the IT Splunk route
- Select the
Routingsubmenu in the top nav and clickData Routes - Expand
palo2ITsplunk
Ah, they followed your lead. IT configured their own Destination splunk:itsplunk (which we can see on the course map). They also configured their Route to simply passthru everything to their Splunk instance. Here’s something new, they filtered the Route based on __inputID.startsWith(’syslog:paloalto’). This means that any other future traffic, say Windows event traffic, wouldn’t use this Route.
Let’s change the Pipeline so that it calls our new cribl-palo-alto-networks Pack.
important
Add our Pack to the route
- Click the dropdown for
pipeline - Select
PACK cribl-palo-alto-networks (Palo Alto Networks) - Click
Save
Another job done. Well almost. Again, if you believe that everything is working, then yeah – we’re done. However, if you like to see proof, then let’s go check that our newly added Pack is reducing the Palo Alto traffic log size, then we can be done.
